

There is a reason why phishing is usually at the top of the list for security awareness training. For the last decade or two, it has been the main delivery method for all types of attacks. Ransomware, credential...

In 2020, smishing rose by 328%, and during the first six months of 2021, it skyrocketed nearly 700% more. Phishing via SMS has become a big risk area. Especially as companies adjust data security to a more remote and...

How often is often enough to improve your team’s cybersecurity awareness? It turns out that training every four months is the “sweet spot.” This is when you see more consistent results in your IT security.

During the first six months of 2021, the number of IoT cyberattacks was up by 135% over the prior year.It’s estimated that over 25% of cyberattacks against businesses involve IoT devices.
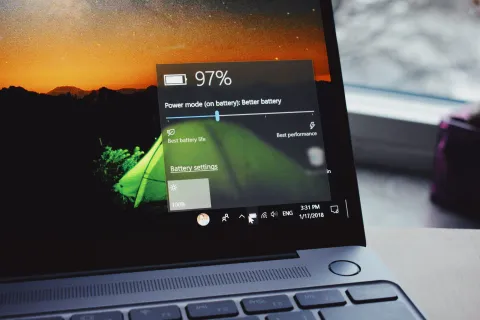
Seeing your laptop’s battery capacity shrink can be frustrating. But there are several things you can do to increase the time you can go without needing to plug it in.

“Hybrid office” is the new buzzword you’ll hear used in business discussions. It’s the mix of having employees both working at the office and working from home. This has become more than a buzzword and is now...

How do you protect your online accounts, data, and business operations? One of the best ways is with multi-factor authentication. It provides a significant barrier to cybercriminals even if they have a legitimate...

Over half of all web searches are also now conducted from a mobile device rather than a desktop PC. This has caused mobile devices to become more targeted over the past few years. As hackers realize they’re...

One of the most important applications we choose is our internet browser. When on a computer or a mobile device, we work in that most of the time because many applications are now cloud-based, so accessing them means...

